Single sign-on (SSO) is an important element in the complex structure of an effective security program.
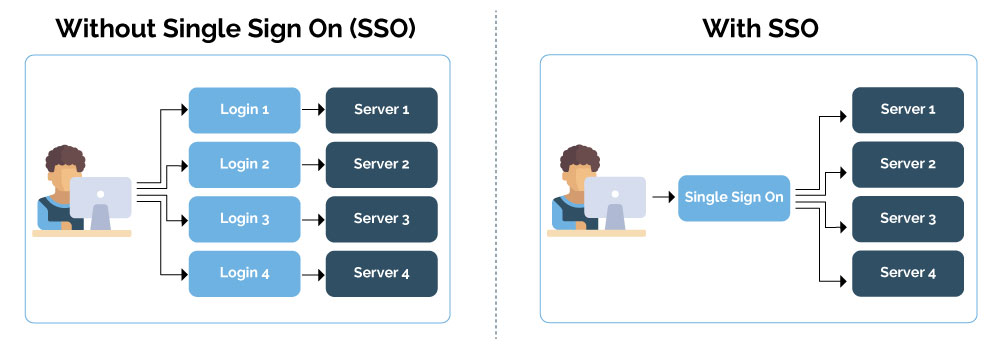
It is a service that gives a user access to multiple network destinations by entering only one login, one username, and one password. Simplifying the login process streamlines workflow and adds a layer of safety by reducing the likelihood of error. If, for example, a user typically accesses four applications during a work session, going through four login routines multiplies the possibility of mistakes and consumes time. However, while SSO enhances ease of access, it also presents some risk.
How SSO works
The service authenticates the access privileges for all the applications a user has rights to and requires no additional actions when switching between them. The application server gathers the user’s credentials from a dedicated SSO policy server and checks the person against a user directory.
A number of login processes, access methods, and system configurations are available, allowing companies to choose an SSO system that best suits their needs and allows for suitable modifications. Moreover, as digital transformation advances, these options will become increasingly complex.
Not only does SSO eliminate tasks, but it also helps with such functions as user-activity management and user-account oversight. However, it also carries a major security risk. A hacker who is able to gain control of a user’s credentials may be able to penetrate every application to which the user has access. This calls for constant attention to password security and diligent protection of usernames, as well as careful online browsing restrictions and stringent protection of email.
SSO capabilities are supplied by identity providers. These entities and their offerings are not alike and choosing the right ones are important decisions that should not be made without expert counsel. A key objective in making a selection is the ability to serve a broad range of users, but it may be necessary to add another authentication system to cover everyone in the organization.
 Advantages of SSO
Advantages of SSO
- Reduces password fatigue. Remembering one password instead of many makes users’ lives easier. As a tangential benefit, it gives users greater incentive to come up with strong passwords.
- Simplifies username and password management. When changes of personnel take place, SSO reduces both IT effort and opportunities for mistakes. Employees leaving the organization relinquish their login privileges.
- Improves identity protection. With SSO, companies can strengthen identity security with techniques such as two-factor authentication (2FA) and multifactor authentication (MFA).
- Increases speed where it is most needed. In settings such as hospitals, defense industries, and emergency services, where large numbers of people and departments demand rapid and unfettered access to the same applications, SSO is especially helpful. In such cases, preventing errors and malware intrusion can be the difference between life and death.
- Relieves help desk workloads. Fewer users calling for help with lost passwords saves money and improves security.
- Reduces security risks for your customers, vendors, and partner entities. Connections between allied companies always present vulnerabilities, which SSO can reduce.
- Effective SSO solutions are available. There is no reason for any organization to create its own system or to develop deep SSO expertise. RenovoData’s consultants understand available offerings and can help identify the best choices for your company.
SSO’s challenges
- Extra-strong passwords must be enforced. If an SSO account is cracked, others under the same authentication can also be endangered.
- When SSO is down, access to all connected sites is stopped. This is a big reason to exercise great care in choosing an SSO system. It must be exceptionally reliable and plans should be in place for dealing with breakdowns.
- What’s more, when your identity provider goes down, your SSO does too. The provider’s vulnerability to any kind of interruption becomes your vulnerability as well, and it is probably beyond your control. Once again, the choice of vendors is critical.
- If a hacker breaches your identity provider user account, all your linked systems could be open to attack. This can be a classic single point of failure and should be headed off in the planning process. On the plus side, high-quality identity providers have top-notch security.
- SSO can take longer than expected to set up. Each environment is different, so added steps in implementation can crop up. One example is the task linking the identity provider to the service provider.
- SSO is risky for multi-user computers. What happens when one user is logged in and another user needs to use the machine?
- Reduced sign-on (RSO) may be needed to accommodate different levels of access. With RSO, additional authentication servers may be required.
- SSO using social networking services can create conflict. This can be the case with workplaces that block social media sites and government connections where censorship is involved.
- Some SSO-linked sites may give their user data to third-party entities. This is an area requiring careful attention.
These are subjects of concern, but none of them is insurmountable. The advantages of SSO significantly outweigh the reasons for caution, but expert professional guidance during planning and implementation is necessary to reap the benefits while minimizing the downsides.
If you are considering a new or upgraded SSO capability, RenovoData can help you weigh your options.
RenovoData is a leading regulatory-compliant, cloud data protection IT services company. Our solutions range from File and Database Backup, Server Recovery, Disaster Recovery as a Service (DRaaS), Custom Cloud Hosting and Consulting solutions for on-premises and hosted environments.